OWASP Accepts Tool For Re-use, Acknowledges as ‘Best Practice’
When a team of ITX developers recently created – and contributed – a new integration to the Open Web Application Security Project’s (OWASP) threat modeling tool (Threat Dragon), they were simply living the company’s culture. Continuous innovation, thriving together, and giving back to the community are pillars of the ITX value system.
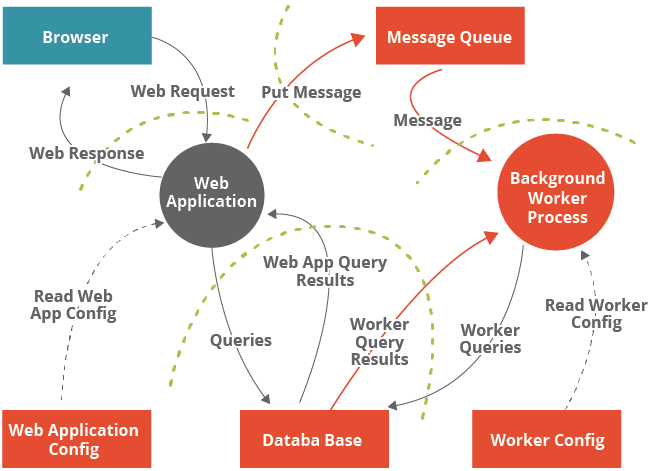
The integration automatically pushes open, non-mitigated security threats created in Threat Dragon directly into our Jira backlog. ITX contributed the integration back to OWASP because we know there are a lot of dev teams in our community using Jira to manage their product backlog – especially if they’re doing it in an Agile mindset.
OWASP has accepted the contribution, even acknowledging ITX as a “Company Collaborator” and posting the integration as a best practice on its website.
“In making this contribution to our Industry, we feel we’re supporting OWASP’s mission,” said ITX VP of IT Services and Security Jonathan Coupal. “We’re working right alongside them to improve application security – not for any self-serving purpose, but in the pursuit of knowledge and knowledge sharing.”
The Integration
Sounds simple enough, but any opportunity to automate an otherwise manual task is not only a timesaver; it serves as a barrier to human error creeping into the process. What’s more, the automation ensures that all threats flow gracefully into the Jira system.
In fact, the integration flows both ways. Because each threat is logged in to Jira, it receives a unique Jira identifier. So the next time a dev team member or security analyst opens the threat model, they are immediately aware that the threat has already been synchronized into Jira.
The impact is huge. But to truly appreciate it, it’s important to first understand ITX’s two-pronged approach to application security through risk-based threat modeling.
In a way, it’s like ‘value signaling.’ We value application security, so much so that we developed a best practice to design it into the products we build while taking the time to educate our clients as to outstanding, unmitigated risks and the costs associated with addressing them – or not.
— Jonathan Coupal, ITX VP of IT Services and Security
Threat Modeling the ITX Way
Threat modeling is a risk-based approach to designing secure applications and systems. The idea is to take the necessary steps to identify possible threats so that you can develop mitigations to them. As the value of digital assets increases, the hacks that threaten them grow more sophisticated, and more sinister. As organizations deepen their awareness of potential exposure and corresponding liabilities, software development and data security teams need increasingly effective ways to build security into their software.
At ITX, we approach application security in two key ways.
First is vulnerability and penetration testing. Essentially, we commission a team of “white hat” hackers to break into an app or website we’re building. It is more of a post-launch, quality assurance technique in which our hackers look for gaps and weaknesses in the app or website that undermine its security.
Second is a more design-driven approach, which allows developers to build security features into the product as it is being designed. Using the OWASP-sponsored Threat Dragon tool, we build a model of the application in a Data Flow Diagram. Our developers’ attention is directed primarily to higher-risk areas of the application as the data flows through it, particularly as it crosses trust boundaries. With CT scan-like precision, we monitor the flow of data to pinpoint vulnerable locations in the model where our data is subject to attack.
By designing security into the app pre-build, we present our clients with the opportunity to think about their data assets that need protection, the value of those assets, and the risks associated with threats to them. We generate reports directly out of Threat Dragon that present easy-to-digest summaries of all the threats we’re designing for, all the ones we’ve already mitigated, and – perhaps most valuable of all – the unmitigated threats that the client can choose to address.
The conversation sounds a bit like this:
- Ok, so we will be building this app/web platform/software product.
- What can go wrong?
- How might we be attacked?
- What’s our exposure if/when we are?
- How do we mitigate our risk? (note, we don’t use prevent here)
- How do we fix it if we fail to mitigate the threat?
- What steps can we take to design additional security features and add them to our backlog?
- How can we test to ensure that we did a good job?
Our design-driven approach to application security immediately escalates awareness of potential threats – and the proposed mitigation – to the client/product owner’s attention. Armed with this information, the client has both the burden and opportunity to decide what level of risk they are willing to tolerate, and how much budget they’re willing to part with to defend their data from attack as it flows through the app.
From the ITX perspective, our approach to application security gives us an incredible opportunity to demonstrate Mastery to our customers.
“In a way, it’s like ‘value signaling,’” Coupal adds. “We value application security, so much so that we developed a best practice to design it into the products we build while taking the time to educate our clients as to outstanding, unmitigated risks and the costs associated with addressing them – or not.
The decision whether and when to act rests entirely with the client. The ITX development team has informed their client by identifying potential threat risks and the costs associated with them. By delivering this information in advance of the product’s next release we’re adding value to an already strong relationship.
“In my experience,” Coupal adds, “customers want to know what their risks are ahead of time – even if they’re not choosing to resolve them. Providing our customers with that choice is a big part of how we think about designing security, as well.”
In making this contribution to our Industry, we feel we’re supporting OWASP’s mission. We’re working right alongside them to improve application security – not for any self-serving purpose, but in the pursuit of knowledge and knowledge sharing.
— Jonathan Coupal, ITX VP of IT Services and Security
Solving our clients’ business problems through technology is what we do at ITX. Living our values is how we get the job done. By combining threat modeling and backlog management with a design-driven approach, we demonstrate not only the value we place in application security. Perhaps even more than that, it speaks to how we embed our culture into the value we deliver to our clients.